AI-Powered Key Takeaways
Introduction
Android apps are central to modern life, serving needs from social networking and shopping to banking and fitness. As these apps manage sensitive user data, secure access through reliable authentication mechanisms is essential.
Biometric authentication, encompassing fingerprint scanning and facial recognition, is increasingly common in Android apps. Given its widespread use, rigorous testing of these authentication features is critical to ensure security and a smooth user experience. However, validating these complex systems across various devices and operating systems presents significant QA challenges.
This blog will discuss the importance of testing biometric authentication and the challenges of testing these systems in real time.
Benefits of Biometric Authentication Testing on Android Devices
The rapid expansion of Android apps across various sectors—such as financial services, personal communication, and health data—has made secure access essential. Frequent logins can lead to password fatigue, making biometric authentication an attractive solution. Methods like fingerprint, facial, or iris recognition provide a seamless, password-free way to access apps while safeguarding data through unique biological identifiers.
When integrated effectively, biometric authentication achieves both enhanced security and user convenience. Here are some critical applications of biometric authentication:
- Enterprise Apps: Facilitates employee login and access-based approvals for confidential documents.
- Health Apps: Protects medical records and insurance claim information.
- Financial Apps: Secures sensitive banking information and transaction approvals through identity verification.
- Retail Apps: Authorizes payments.
- Government Apps: Verifies citizen identities.
- Travel Apps: Ensures secure check-ins and hotel room access.
Biometric authentication testing significantly boosts both security and convenience across a wide range of mobile applications.
Read: Biometric Authentication Testing for iOS Apps
Challenges in Biometric Authentication Testing
Thorough testing is crucial for mobile and web apps to ensure a seamless user experience while maintaining security. This is especially important for apps in sectors like BFSI, law, fintech, healthcare, and government, where fingerprint scanners on Android and iOS devices need rigorous evaluation.
Biometric authentication requires real device testing, as simulators cannot accurately replicate the fingerprint scanning. This introduces several challenges:
- Simulator Limitations: Testing biometric authentication on simulators is problematic since they cannot capture real biometric data.
- Limited Test Coverage: Testing is restricted to the available real devices cloud with fingerprint scanning capabilities, which may limit coverage.
While using cloud-based real devices can help mitigate some of these limitations, capturing fingerprints in the app remains challenging, necessitating a robust infrastructure for practical testing.
Advantages of Biometric Authentication Over Traditional Username/Password Login
Biometric authentication surpasses traditional username/password methods in several key areas, offering notable benefits that enhance security, user experience, and convenience. Here's why biometric authentication is often preferred:
- Enhanced Security: Biometric data, including fingerprints or facial features, are unique to individuals, making unauthorized access considerably more complex and improving overall security.
- Eliminates Password Issues: With biometric authentication, users no longer need to remember or manage passwords, reducing risks related to weak passwords, reuse, and forgetfulness.
- Convenience: Biometric methods provide a seamless user experience, allowing quick access to devices or applications through simple fingerprint or facial scans, thus avoiding the hassle of password entry.
- Speed and Efficiency: Biometric authentication is faster and more efficient than typing passwords. It enables users to unlock devices or log in with a touch or glance, saving time and effort.
- Mitigates Phishing and Brute Force Attacks: By eliminating the need for passwords, biometric authentication reduces the effectiveness of phishing attacks and decreases the probability of succeeding in brute force attacks, where attackers try to guess passwords.
Also read: 10 steps to perform mobile app security testing?
Understanding Android Biometrics
Android Biometrics encompasses a variety of sensors on Android devices that can scan biometric data such as fingerprints, retinas, and facial structures. These sensors provide a secure way for users to verify their identity, adding a layer of protection for sensitive data within Android applications.
How Does Android Biometrics Work?
Like other biometric systems, Android Biometrics scans and stores digital fingerprints or other biometric data for authentication. When a user initiates the authentication process, the sensor captures the biometric information, compares it to the stored data, and verifies the user's identity.
Android Biometrics may use dedicated hardware components to enhance security depending on the device and sensor type. These components help ensure that biometric data is securely stored and processed, reducing the risk of unauthorized access.
Supported Devices
Android's extensive ecosystem includes many devices equipped with biometric sensors. Most modern Android smartphones and tablets offer some form of biometric authentication. Device manufacturers may refer to these features differently: for instance, some use terms like Face Unlock and Fingerprint Unlock, while others use Facial Recognition and Fingerprint Recognition.
Check out: Why should you invest in the Security Testing of Mobile Applications?
Testing Biometric Authentication on Android with HeadSpin
Installing HeadSpin's Android Biometrics SDK
To integrate HeadSpin's Android biometrics SDK, follow these steps:
1. Download the SDK: Access the download and documentation links from the HeadSpin Settings page.
2. Prepare Your Project: In Android Studio, create a directory named source/main/libs within your app's directory.
3.Add the SDK File: Download the instruments-release.aar file and place it in the libs directory.
5. Configure Repositories: If the library is not found, add flatDir to the Repositories block, pointing to your libraries directory.
Summing Up
Biometric technology, especially fingerprint scanning, has significantly advanced device security by offering speed, enhanced protection, and user-friendly experiences without the need for passwords. This innovation provides a robust and efficient safeguard for personal information.
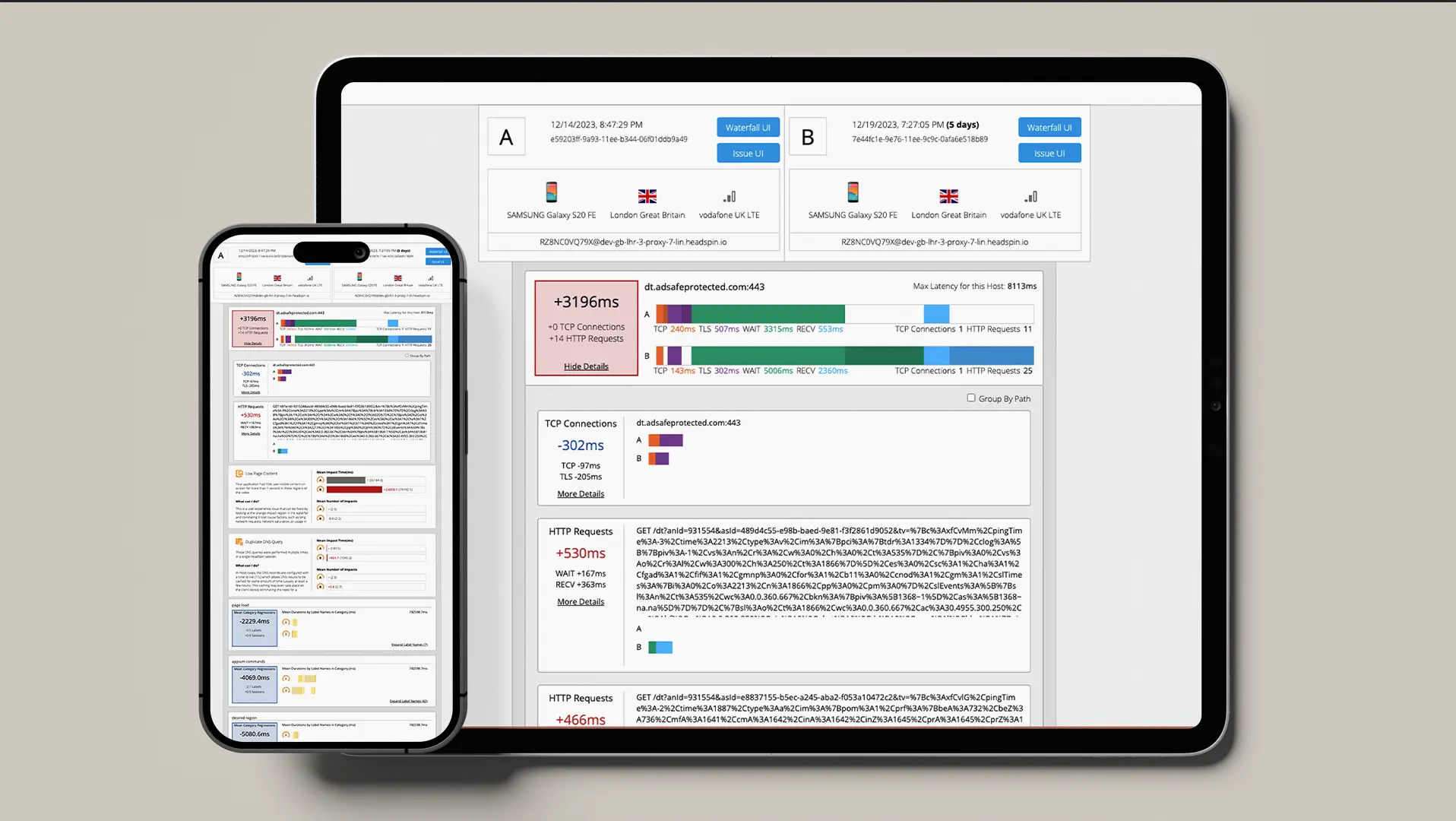
While integrating biometric authentication into Android apps has become standard, testing these features presents challenges, mainly when using traditional tools like Appium. Development teams use HeadSpin's cloud-based testing platform, which offers precise biometric testing across various device-OS combinations, to address these challenges.
HeadSpin's biometric authentication feature allows for comprehensive testing of fingerprint scanning functionality on real devices without needing actual fingerprint scans. This capability ensures that Android applications are both reliable and secure. Consider adding HeadSpin to your testing toolkit to achieve thorough and effective biometric authentication testing.
FAQs
Q1. How do biometrics and fingerprints differ?
Ans: Biometric technology uses unique physical or behavioral traits to identify individuals, which are generally challenging to replicate. Fingerprints are a specific type of biometric, based on the exclusive patterns of ridges and valleys on an individual's fingerprints to provide identification.
Q2. What is biometric authentication on iOS?
Ans: Biometric authentication on iOS is a security process that verifies a user's identity through distinct physical traits, like fingerprints as well as facial features. The system stores this biometric data to authenticate the user when securely accessing their device or applications.
Q3. How can I check whether biometric authentication is available on Android?
Ans: To verify biometric authentication availability on Android, check the supported authentication methods for your app. Use the canAuthenticate() method with a bitwise combination of the types specified in the setAllowedAuthenticators() method to determine if biometric authentication is supported.


























.png)

























-1280X720-Final-2.jpg)